Capture Formats
If you are happy with your capture’s/stream’s file type, you can safely skip this section.
When you send packets to a file or pipe, you are also sending the packet and file headers. Normally, you will not need to care about the file format of your packets. This section exists for when it does matter.
If you capture no packets and send to xxd, you can see just the file header for any capture type.
An easy way to capture no packets is to filter by unused ipx in your capture filter.
In this example, we use -F pcap for the pcap file type.
bash$ tshark -f ipx -a duration:1 -F pcap -w - 2>/dev/null | xxd -u
00000000: D4C3 B2A1 0200 0400 0000 0000 0000 0000 ................
00000010: 0000 0400 0100 0000
The first 24 bytes should look like the logo up left (capture headers may differ on your system).
Of those, the first 4 bytes, D4C3 B2A1, are the magic bytes that identify the capture as a pcap file.
Packet-Foo has a good article on the difference between file header and file bytes that goes into more depth.
Table of Contents
- Format Usage
- captype
- Pcap Format
- Pcap Deconstruction
- Pcapng Format
- Magic Numbers
- Available Save Formats
- Capture Headers
Background on how capture formats are used
Get the capture's file type
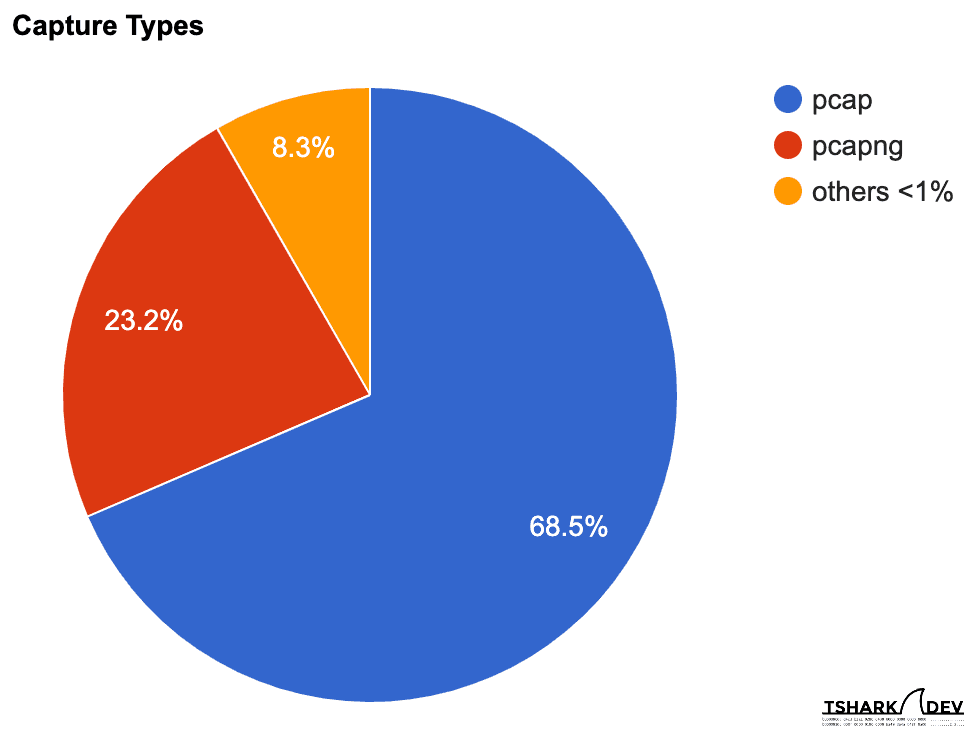
Libpcap format, industry default
Which bytes mean what
Format, The Next Generation
The first 4-16 bytes of a capture
Bytes in each capture format that are not packets
Bytes in each capture format that are not packets